What is the difference between an hids and a firewall – In the ever-evolving landscape of cybersecurity, the distinction between an intrusion detection system (IDS) and a firewall takes center stage. These two guardians of network security play distinct yet complementary roles in safeguarding systems and data from malicious threats. This comprehensive guide delves into the intricacies of each system, highlighting their differences, advantages, and applications.
Introduction
An intrusion detection system (IDS) and a firewall are two essential components of a comprehensive network security strategy. While both systems are designed to protect against unauthorized access and malicious activity, they differ in their primary functions, detection mechanisms, and scope of coverage.
Detection and Response Mechanisms
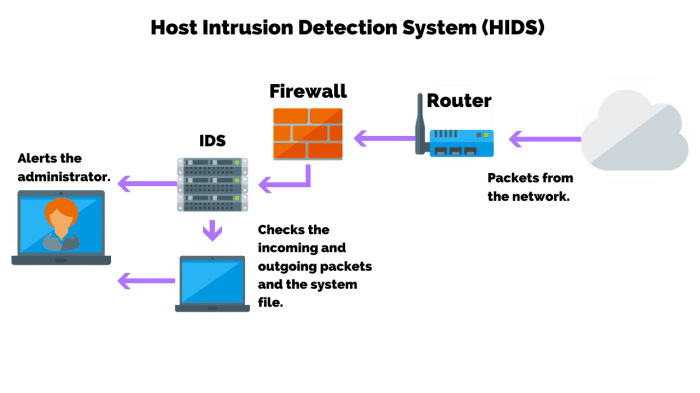
An IDS is designed to detect suspicious activity and issue alerts or take automated actions based on predefined rules. It typically uses a variety of detection methods, including signature-based detection, anomaly-based detection, and behavioral analysis. A firewall, on the other hand, is a network security device that monitors and controls incoming and outgoing network traffic based on a set of predefined rules.
It blocks unauthorized traffic and allows legitimate traffic to pass through.
Scope and Coverage, What is the difference between an hids and a firewall
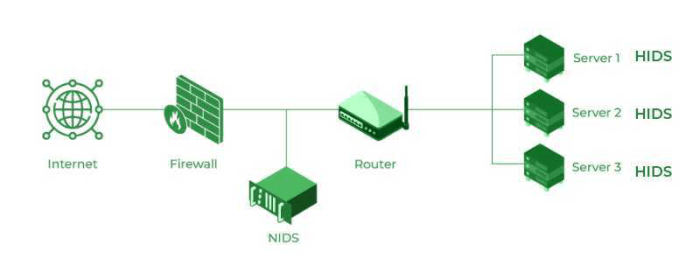
An IDS monitors network traffic for suspicious activity, typically within a specific network segment or host. It can detect threats that have already penetrated the network and can help identify the source of an attack. A firewall, on the other hand, monitors and controls traffic at the network perimeter, blocking unauthorized access to the network and its resources.
Implementation and Deployment
An IDS can be deployed in various ways, including inline, passive, or host-based. Inline IDS are deployed in the network path and can actively block or drop malicious traffic. Passive IDS monitor network traffic without interfering with it. Host-based IDS are installed on individual hosts and monitor activities within the host system.
Firewalls are typically deployed at the network perimeter, either as hardware appliances or software-based solutions.
Management and Monitoring
An IDS and a firewall require regular monitoring and maintenance to ensure their effectiveness. IDS management typically involves defining and tuning detection rules, analyzing alerts, and responding to incidents. Firewall management includes configuring rules, monitoring traffic logs, and performing regular updates.
Advantages and Disadvantages
IDS and firewalls offer different advantages and disadvantages. IDS can provide in-depth visibility into network traffic and can detect threats that have already bypassed the firewall. However, they can also generate false positives and can be complex to manage. Firewalls are effective at blocking unauthorized access and can be relatively easy to implement.
However, they may not be able to detect all types of threats, such as zero-day attacks.
Use Cases and Applications
IDS and firewalls are used in a variety of scenarios. IDS can be used to monitor critical systems, detect advanced persistent threats (APTs), and investigate security incidents. Firewalls are used to protect networks from unauthorized access, prevent data breaches, and comply with regulatory requirements.
FAQ Guide: What Is The Difference Between An Hids And A Firewall
What is the primary difference between an IDS and a firewall?
An IDS detects and responds to malicious activity within a network, while a firewall prevents unauthorized access to and from the network.
How does an IDS detect threats?
IDSs use various techniques, including signature-based detection, anomaly detection, and behavioral analysis, to identify suspicious activities.
What is the scope of protection provided by a firewall?
Firewalls monitor and control network traffic at specific points, such as network boundaries or individual hosts.
How are IDS and firewalls typically deployed?
IDSs can be deployed on individual hosts or as network-wide sensors, while firewalls are typically deployed at network gateways or perimeters.